How to Automate Azure Resource Groups Deployment
This blog shows you how to automate the creation and removal of Azure Resource Groups based on Azure AD Group membership in a Demo Azure subscription. To help you, I developed the following PowerShell script, which is deployed as a Runbook in an Azure Automation account and scheduled to run once a day.
As new users are added to a designated Azure Active Directory security group, resource groups are automatically provisioned for them when the script runs. They are assigned the appropriate AD Role Definition for the resource group. When a user is removed from the Azure AD security group, the resource group and corresponding resources are removed automatically at the next script run.
The script takes a SubscriptionName parameter. The Azure logon process is initiated with a Service Principal Application ID and certificate thumbprint. In the script logic we get the MailNickNames property of the Azure AD group members. We also get the current Resource Groups with names matching the value of the $RGPrefix variable.
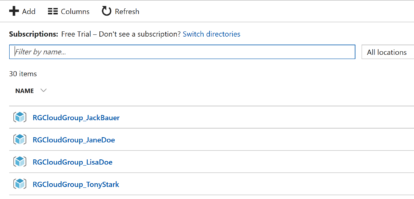
If there are currently no matching resource groups, the script creates resource groups for each of the Azure AD security group member. Each user’s resource group is named by appending the $RGPrefix value with the MailNickName property of the user object. The resource groups are assigned initial tags. And the Owner role definition is assigned to the Azure AD user for the resource group. The following screen shot is an example of Resource Groups created after running the script:
[code language=”PowerShell”]
param(
[parameter(Mandatory=$false)]
[string]$subscriptionName = "free trial"
)
#region Azure Logon
$adAppId = Get-AutomationVariable -Name “AutomationAppId”
$tenantId = Get-AutomationVariable -Name “AutomationTenantId”
$subscriptionId = Get-AutomationVariable -Name "AutomationSubscriptionId”
$cert = Get-AutomationCertificate -Name “AutomationCertificate”
$certThumbprint = ($cert.Thumbprint).ToString()
Login-AzureRmAccount -ServicePrincipal -TenantId $tenantId -ApplicationId $adAppId -CertificateThumbprint $certThumbprint
Connect-AzureAD -TenantId $tenantId -ApplicationId $adAppId -CertificateThumbprint $certThumbprint
Select-AzureRmSubscription -SubscriptionName $subscriptionName
#endregion
$RGPrefix = "RGCloudGroup_"
$Location = "southcentralus"
$cloudGroupObj = Get-AzureADGroup -SearchString "Cloud Group"
#$cloudGroupObj = Get-AzureADGroup -ObjectId "f7351641-0d87-4d6a-adb2-3d060e70cbd7"
$cloudGroupMembers = Get-AzureADGroupMember -ObjectId $cloudGroupObj.ObjectId
$groupMembersDisplayNames=Get-AzureADGroupMember -ObjectId $cloudGroupObj.ObjectId |%{($_.MailNickName)}
$rgNamesSplit=@(Get-AzureRmResourceGroup |? ResourceGroupName -like "*RGCloudGroup_*"| %{$_.ResourceGroupName.Split("_",2)[1]})
if($rgNamesSplit.Count -eq 0){
foreach($cloudGroupMember in $cloudGroupMembers){
$rgsuffix = ($cloudGroupMember.MailNickName)
$clouduser=Get-AzureADUser -SearchString $cloudGroupMember.MailNickName
$tags = @{
CreatedBy = "Automation"
Department = "CloudGroup"
}
$rgObj = New-AzureRmResourceGroup -Name ($RGPrefix + $rgsuffix) -Tag $tags -Location $Location
New-AzureRmRoleAssignment -ResourceGroupName ($rgObj.ResourceGroupName) -RoleDefinitionName Owner -ObjectId $clouduser.ObjectId -ErrorAction SilentlyContinue
}
}else{
$compares=Compare-Object -ReferenceObject $groupMembersDisplayNames -DifferenceObject $rgNamesSplit
foreach($compare in $compares){
if($compare.SideIndicator -eq "<="){
$newMember=$compare.InputObject
$rgsuffix = $newMember
$cloudUser = Get-AzureADUser -SearchString $newMember
$tags = @{
CreatedBy = "Automation"
Department = "CloudGroup"
}
$rg=Get-AzureRmResourceGroup -Name ($RGPrefix + $rgsuffix) -ErrorAction SilentlyContinue
if($rg -eq $null){
$rgObj = New-AzureRmResourceGroup -Name ($RGPrefix + $rgsuffix) -Tag $tags -Location $Location
New-AzureRmRoleAssignment -ResourceGroupName ($rgObj.ResourceGroupName) -RoleDefinitionName Owner -ObjectId $cloudUser.ObjectId -ErrorAction SilentlyContinue
}
}elseif($compare.SideIndicator -eq "=>"){
$removedMember=$compare.InputObject
Remove-AzureRmResourceGroup -Name ($RGPrefix + $removedMember) -Force -ErrorAction SilentlyContinue
}
}
}
#Get-Variable | Remove-Variable -ErrorAction SilentlyContinue
#cls
[/code]
